How To Remove XLoader Malware on mac (Quick Guide)
Before we dive in
Before we dive in, let's make sure you stay safe online. We created SpyHunter because your security matters to us.
Protect your computer today — download SpyHunter right here! Check out our top tips below to keep your computer safe and secure.

Ever worried about the safety of your personal information on your Mac?
XLoader is a malware that has been cleverly disguised to avoid detection and can capture everything from your keystrokes to your most sensitive passwords.
In this article, we’ll examine what makes XLoader particularly risky for Mac users, how it infiltrates your system, and importantly, how you can safeguard your device.
What exactly is XLoader malware?
XLoader is a malicious software program that targets both Windows and macOS systems.
Originally derived from FormBook—a notorious malware specializing in data theft—XLoader inherits and extends its capabilities.

This malware functions primarily as an information stealer, logging keystrokes, and capturing login credentials.
It operates stealthily, making its detection challenging for the average user while affecting a diverse range of systems globally.
Key characteristics of XLoader on macOS
On macOS, XLoader behaves as a powerful info-stealer and keylogger.
It infiltrates systems by obfuscating its presence to evade security. XLoader typically settles into the /Users/[username]/Library/LaunchAgents directory with files that often look randomly named to blend in.
From there, it operates discreetly in the background, recording keystrokes, the user’s clipboard data, and stealing passwords from various applications, including browsers and email clients. This sensitive information can then be exploited in various ways.
XLoader extends its threat to macOS users due to the growing popularity of Apple devices among professionals and regular users alike, thereby incentivizing threat actors to target the platform’s relatively less guarded ecosystem compared to Windows.
The evolution of XLoader from a simple keylogger
XLoader originated as a spin-off of FormBook, which up until its cessation, was heavily employed in cybercrime for capturing data and issuing commands remotely.
FormBook only targeted Windows machines during its active period, whereas its successor XLoader broadened that scope.
While previous versions of the malware were merely a keylogger and credential stealer on Windows, this expanded to macOS, adapting to the dual operating system environment. Now XLoader targets both operating systems.
Since its emergence, XLoader has undergone rapid development, adding features and refining existing ones to increase efficacy and evade detection.
The malware is now sold on dark web forums with different pricing models, highlighting its transition into a full-fledged Malware-as-a-Service (MaaS).
How do Mac users encounter XLoader?
Mac users typically encounter the XLoader malware through sophisticated social engineering techniques.
Cyber criminals carefully craft these methods to disguise the harmful nature of the software, tricking users into downloading and executing it unsuspectingly.
The most common vectors include phishing emails, malicious websites, and deceptive software updates.
Common entry points for XLoader on your Mac
XLoader infiltrates Mac systems mainly through corrupted downloads and spam campaigns. Users may unintentionally download a rogue application thinking it is legitimate, often from unverified sources.
For instance, the latest version of the malware was hidden within a malicious app called OfficeNote that mimics an office productivity app, tricking users into downloading from a deceptive pop-up or advertisement.
The Mac version of the office productivity application is distributed in various ways:
- Freeware sites or third-party app stores often harbor applications bundled with hidden malware like XLoader.
- Peer-to-Peer (P2P) file-sharing networks are common culprits for distributing disguised malware packages.
- Opening emails that seem harmless or clicking on attachments and links in phishing emails can trigger the download of such malicious software.
Remove XLoader using SpyHunter
SpyHunter is adept at removing malware like XLoader due to its specialized malware detection & removal capabilities.
It’s designed to detect various types of malware, including info-stealers like XLoader. SpyHunter updates regularly to handle new threats, ensuring that it can detect and eradicate the latest malware versions.
- Download the app and follow the installation prompts to install it on your macOS.
- Launch SpyHunter and run a full system scan.
- Once XLoader or any other threats are detected, review the scan results. SpyHunter provides detailed information about identified threats.
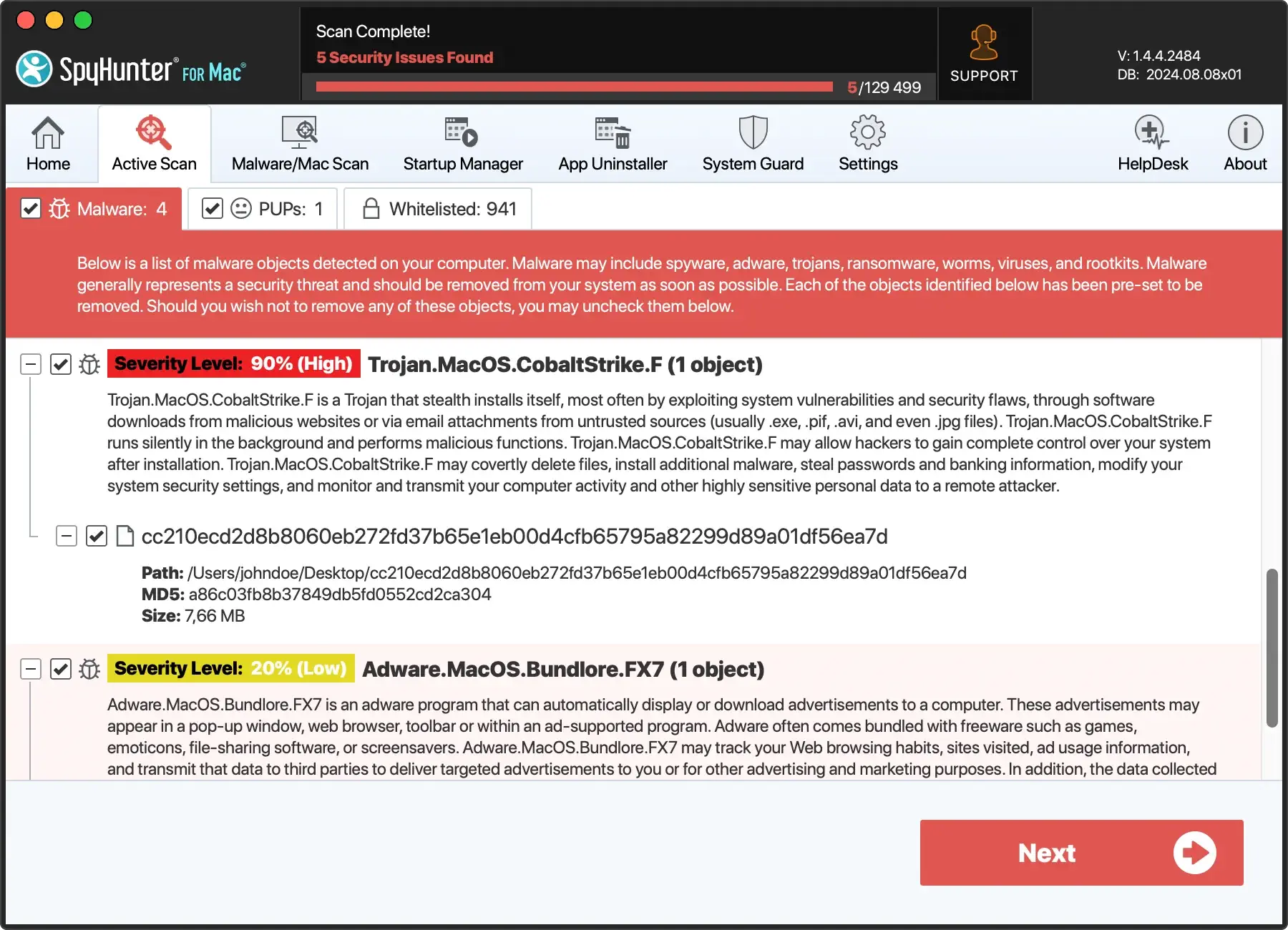
- Click ‘Next’ to remove the detected malware, including XLoader. This process may require a system reboot to complete.
- After cleaning, perform a second scan to ensure all malicious components are eradicated.
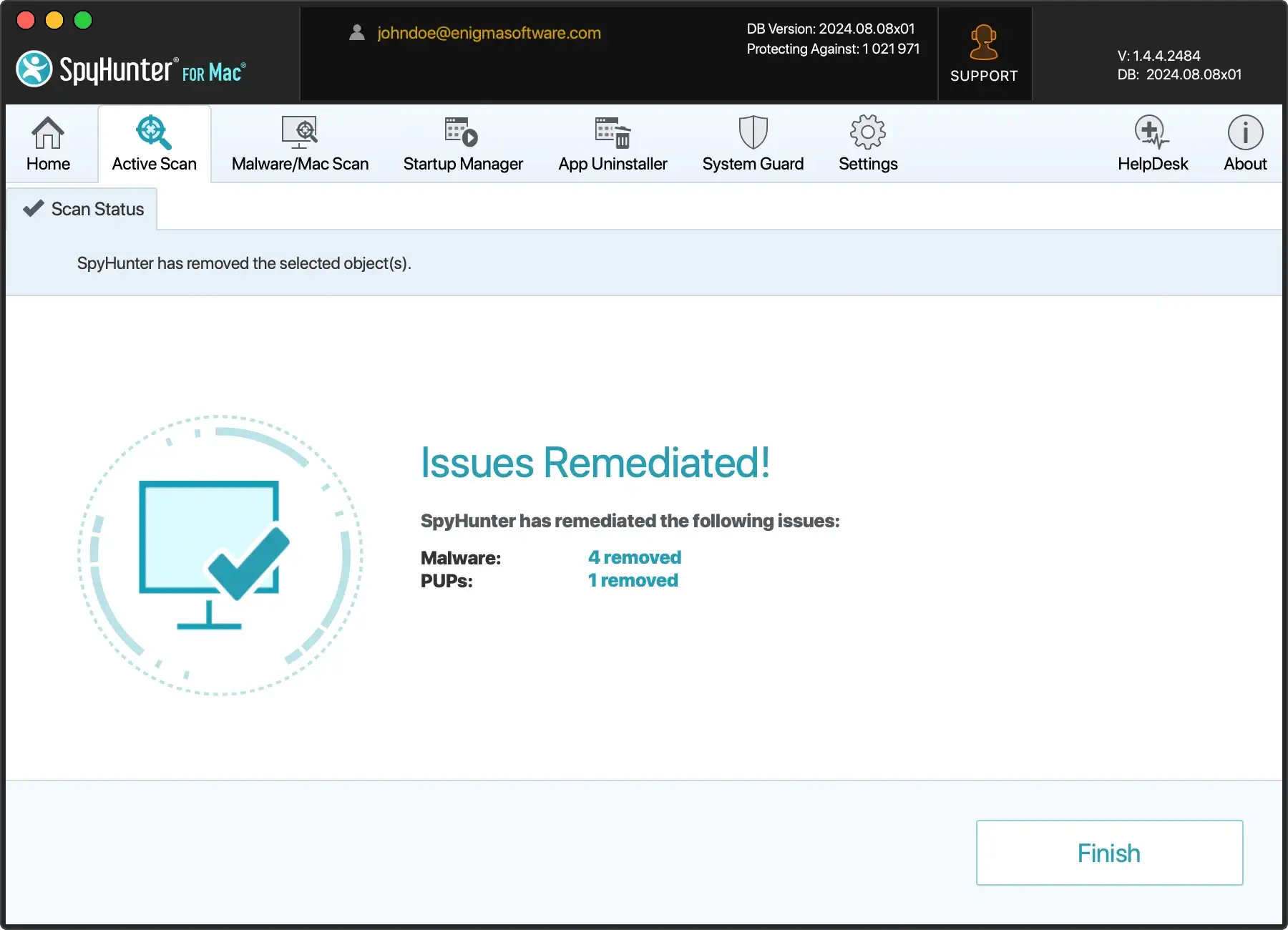
SpyHunter provides real-time monitoring, catching threats immediately as they arise, thus minimizing potential damage.
This proactive approach in cybersecurity ensures users maintain privacy and data integrity, key components often targeted by malware like XLoader.
Step-by-step guide for the manual removal of XLoader
Step 1: Remove malicious apps linked to XLoader
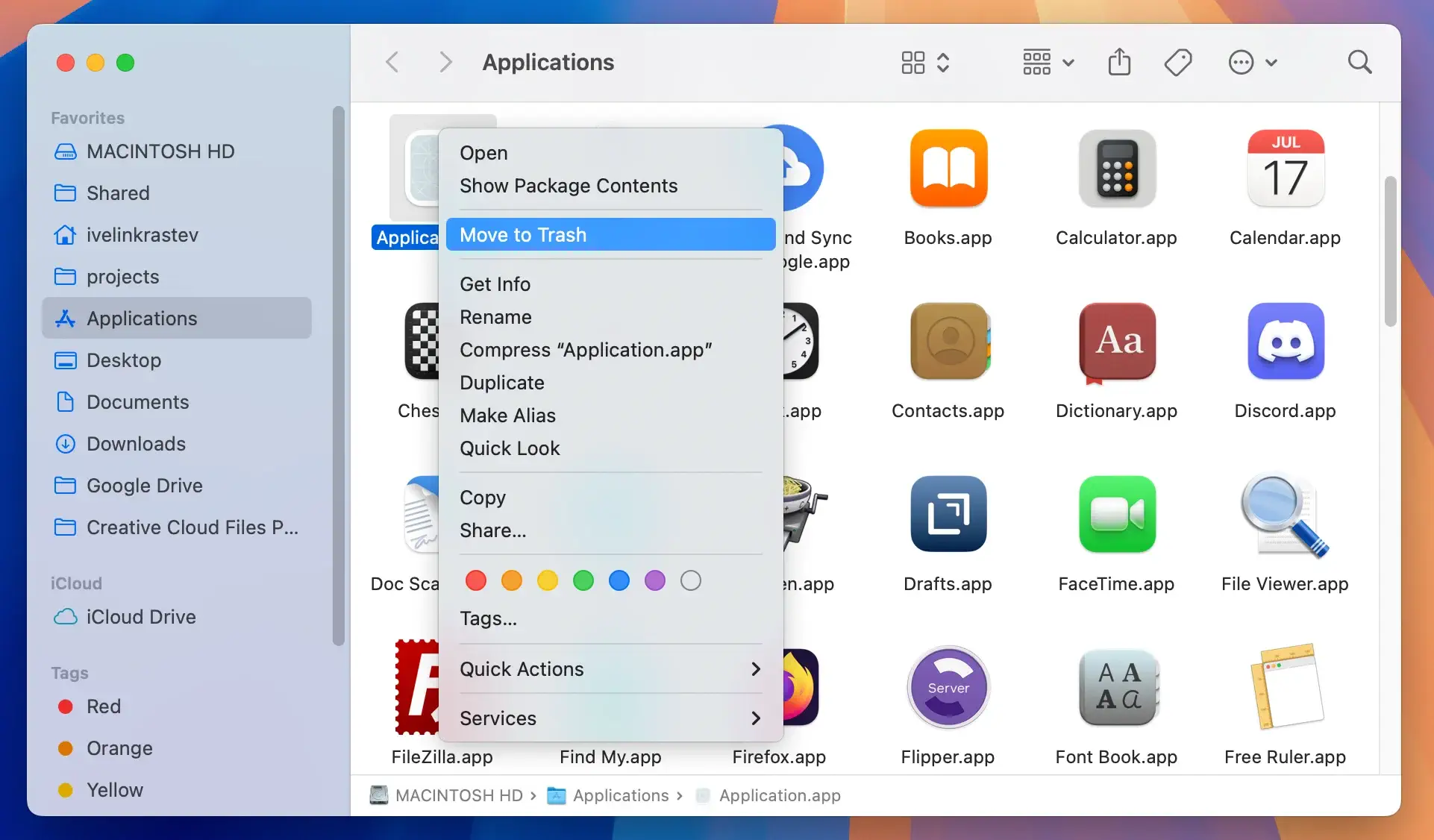
- Open your
Applicationsfolder and look for any app icons named XLoader or any apps you do not remember installing or using. - Drag and drop the suspicious application in the
Trashcan. - Empty the
Trashto remove it completely.
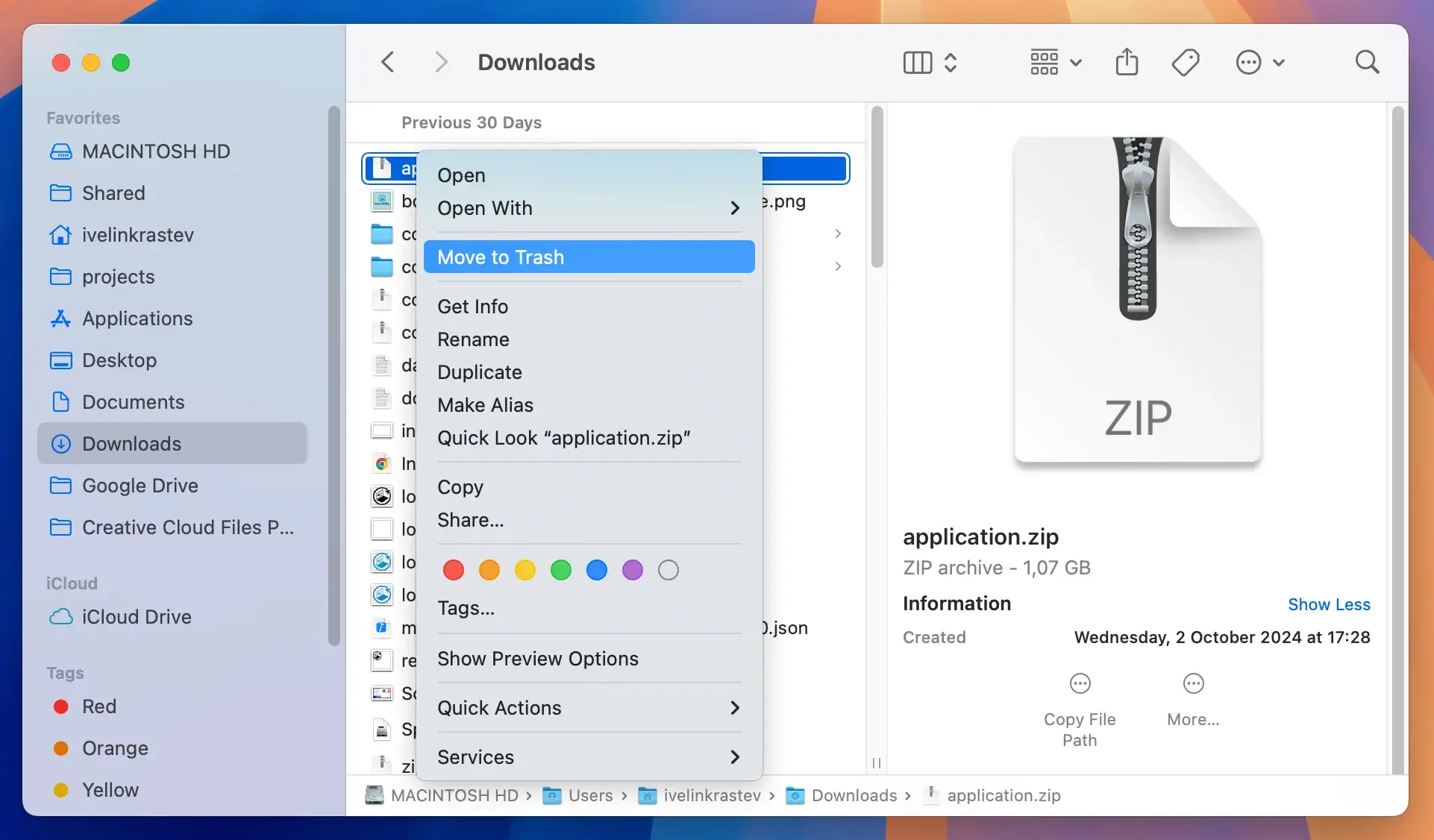
Step 2: Remove files linked to XLoader
- Open a
Finderwindow and click onGo > Go to Folderin the upper menu. - In the dialog box, paste the following locations and delete all files linked to XLoader that you find inside, substituting [username] with your account’s name:
/Users/[username]/Library/LaunchAgents/Library/LaunchAgents//Library/Application Support//Library/LaunchDaemons/~/Library/LaunchAgents/~/Library/Application Support/
- Empty the
Trashafter deleting the files to complete this step.
Preventive measures against future malware attacks
One of the most effective strategies to prevent malware attacks on your Mac is to proactively manage and maintain your system’s security settings.
Ensuring that your operating system and all installed applications are up-to-date with the latest security patches and updates can significantly reduce vulnerabilities. It’s also crucial to enable firewall settings which serve as a barrier between your data and potential threats.
Regularly updating these defenses is key to thwarting attacks before they happen.
Using robust security tools like SpyHunter can further safeguard your Mac from potential threats.
Essential cybersecurity tips for everyday Mac users
Adopting strong, unique passwords for each online account is among the foundational cybersecurity tips.
Utilizing a password manager can assist in generating and storing complex passwords securely.
Additionally, enabling two-factor authentication (2FA) adds an extra layer of security, significantly lowering the risk of unauthorized access even if someone discovers your password.
It’s also a good idea to be cautious about the networks you connect to; public Wi-Fi can be a breeding ground for hackers looking to intercept your data.
Using a virtual private network (VPN) when accessing public internet services can protect your online activities from prying eyes.
Additionally, educating yourself about phishing techniques and being prudent about opening email attachments or clicking on links from unknown sources can protect you from many common cyber threats.