How To Remove Cthulhu Stealer Malware On Mac [Quick Guide]
Before we dive in
Before we dive in, let's make sure you stay safe online. We created SpyHunter because your security matters to us.
Protect your computer today — download SpyHunter right here! Check out our top tips below to keep your computer safe and secure.

Are you worried about the security of your Mac? There’s a new menace that demands your attention.
Known as Cthulhu Stealer, this malware targets macOS users by exploiting system vulnerabilities to steal sensitive data.
What exactly is Cthulhu Stealer, how does it operate, and why is it a significant threat to macOS users? This article dives deep into these questions, offering you a clear picture of the risks involved and practical steps you can take to protect your system from such malicious software.
What is Cthulhu Stealer?
Cthulhu Stealer is a new macOS malware written in Golang that targets macOS hosts, specifically designed to collect sensitive information from Apple users.
Given its Malware-as-a-Service (MaaS) model, and availability for $500 per month, it poses a significant threat to both individual and corporate security.
Cthulhu Stealer operates by infiltrating macOS systems, primarily through phishing or compromised software downloads.
Once installed, it can harvest a wide range of data, including but not limited to, keylogs, browser history, and potentially stored password files. This malware capitalizes on vulnerabilities or uninformed user behaviors to gain unauthorized access and exfiltrate data to servers controlled by malicious actors.
For individuals, the theft of personal information such as passwords or financial data can lead to identity theft and financial fraud.
How does Cthulhu Stealer operate?
Cthulhu Stealer masquerades as normal software, often delivered as an Apple disk image (DMG). This makes it appear trustworthy to unsuspecting users.
The malware is distributed under different disguises, posing as legitimate applications of games. It should be noted that in order to run it, users will need to manually let it past the protection layer provided by Gatekeeper.
The malware brings up a prompt requiring the system password. After obtaining the system password, it swiftly moves to the next target—cryptocurrency wallets.
Users are prompted again, this time to input their MetaMask password. Post these intrusions, the malware uses an open-source tool, Chainbreaker, to access the iCloud Keychain, harvesting stored web and application passwords.
The stolen data, including system information, browser cookies, and cryptocurrency wallet credentials, is then neatly compiled into a text file, compressed into a ZIP archive, and secretly transmitted to a command-and-control server.
Remove Cthulhu Stealer using SpyHunter
When dealing with malware like Cthulhu Stealer, having a reliable anti-malware tool is an indispensable help.
SpyHunter is a powerful anti-malware application for Macs that can detect and remove a wide range of malware, from browser hijackers and adware to more significant threats like infostealers.
- Download the app here and install it on your Mac.
- Launch SpyHunter and then select a full scan of your Mac from the app’s main menu.
- Wait for the scan to complete and then examine the list of results, making sure every item detected is selected for removal.
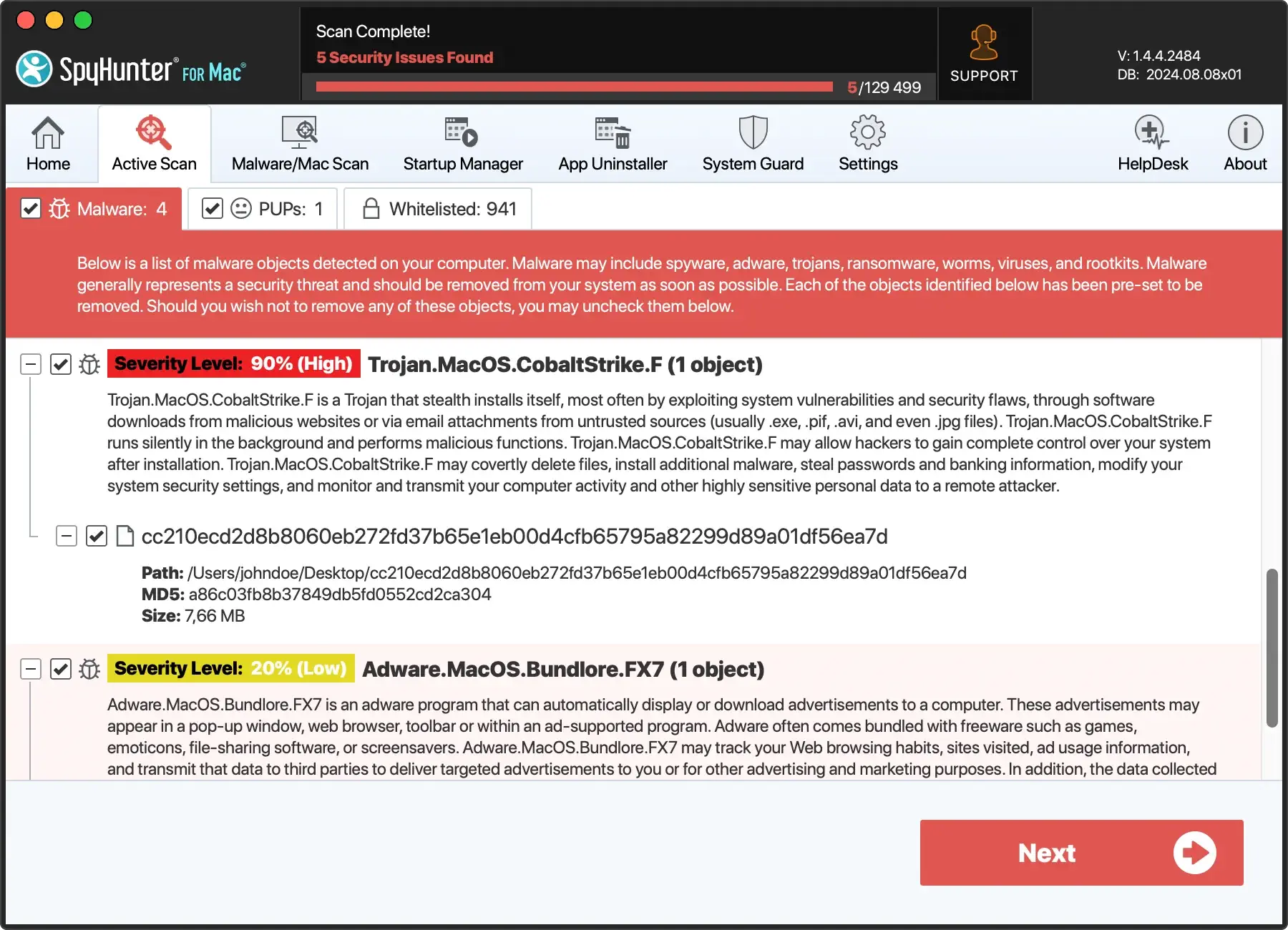
- Proceed to remove all detected threats and enjoy a safer experience on your Mac.
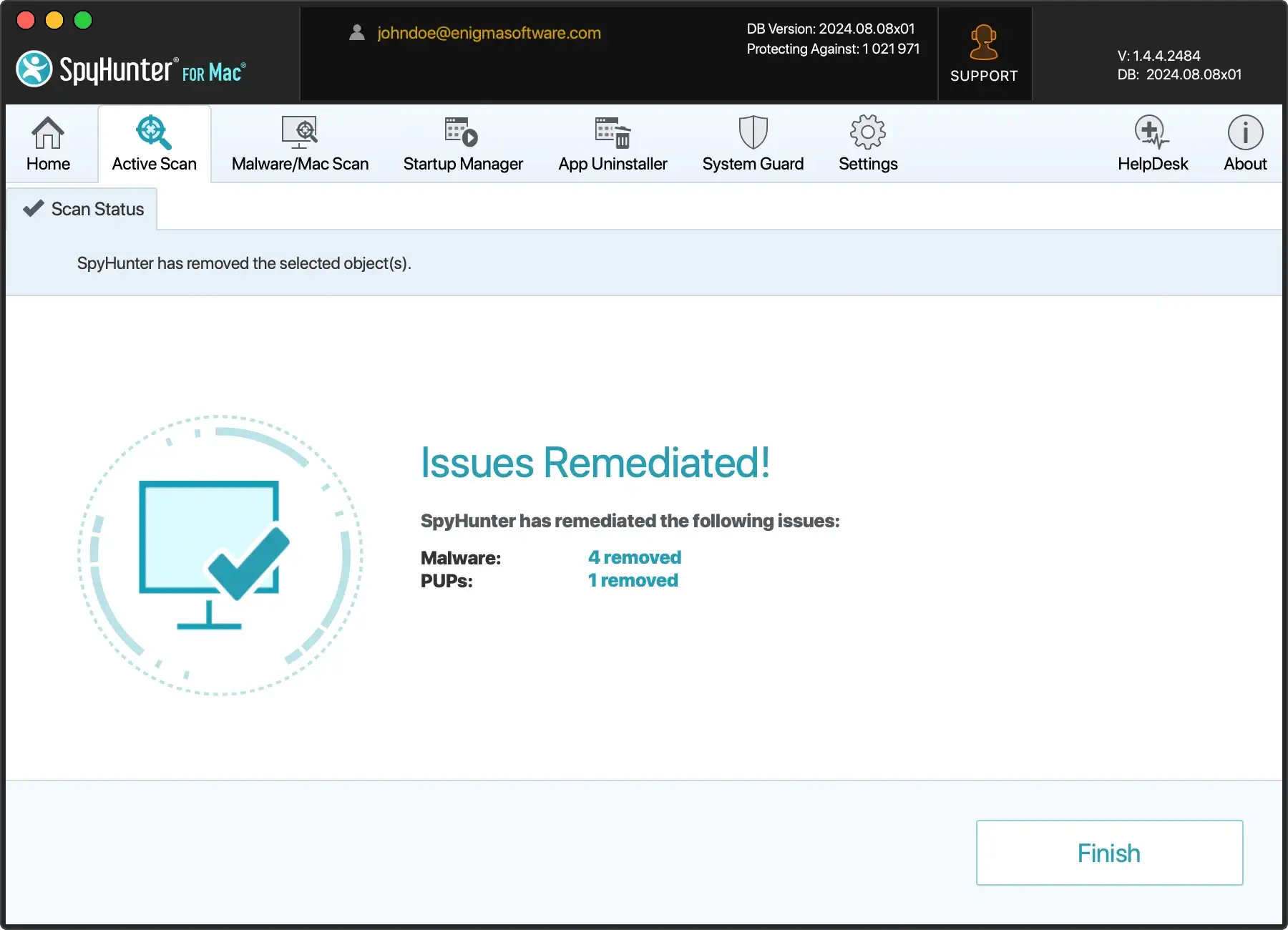
Steps to manually remove Cthulhu Stealer on Mac
1. Force quit all suspicious processes
Begin with killing any processes on your Mac that may be connected to Cthulhu Stealer.
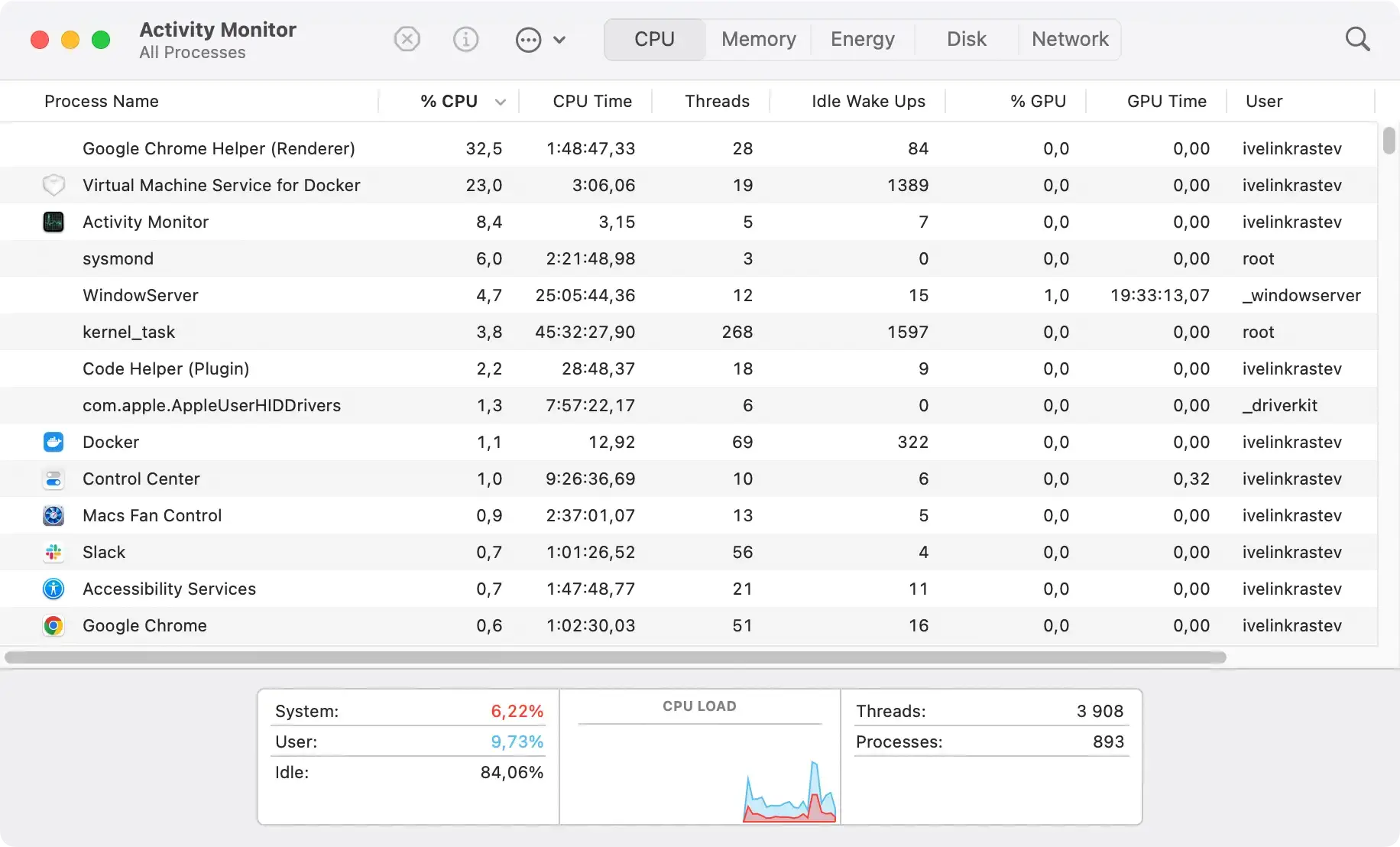
- Open
Activity MonitorfromApplications > Utilities. - Examine the list of active processes and look for any process names that seem odd, unfamiliar, or suspicious.
- Select those processes and force quit them using the
Stopbutton in the upper part of theActivity Monitorwindow. - Confirm the action for each process using the button in the pop-up when you try to force quit any process.
2. Remove any suspicious applications
Proceed with removing any suspicious applications that may be linked with the Cthulhu Stealer malware.
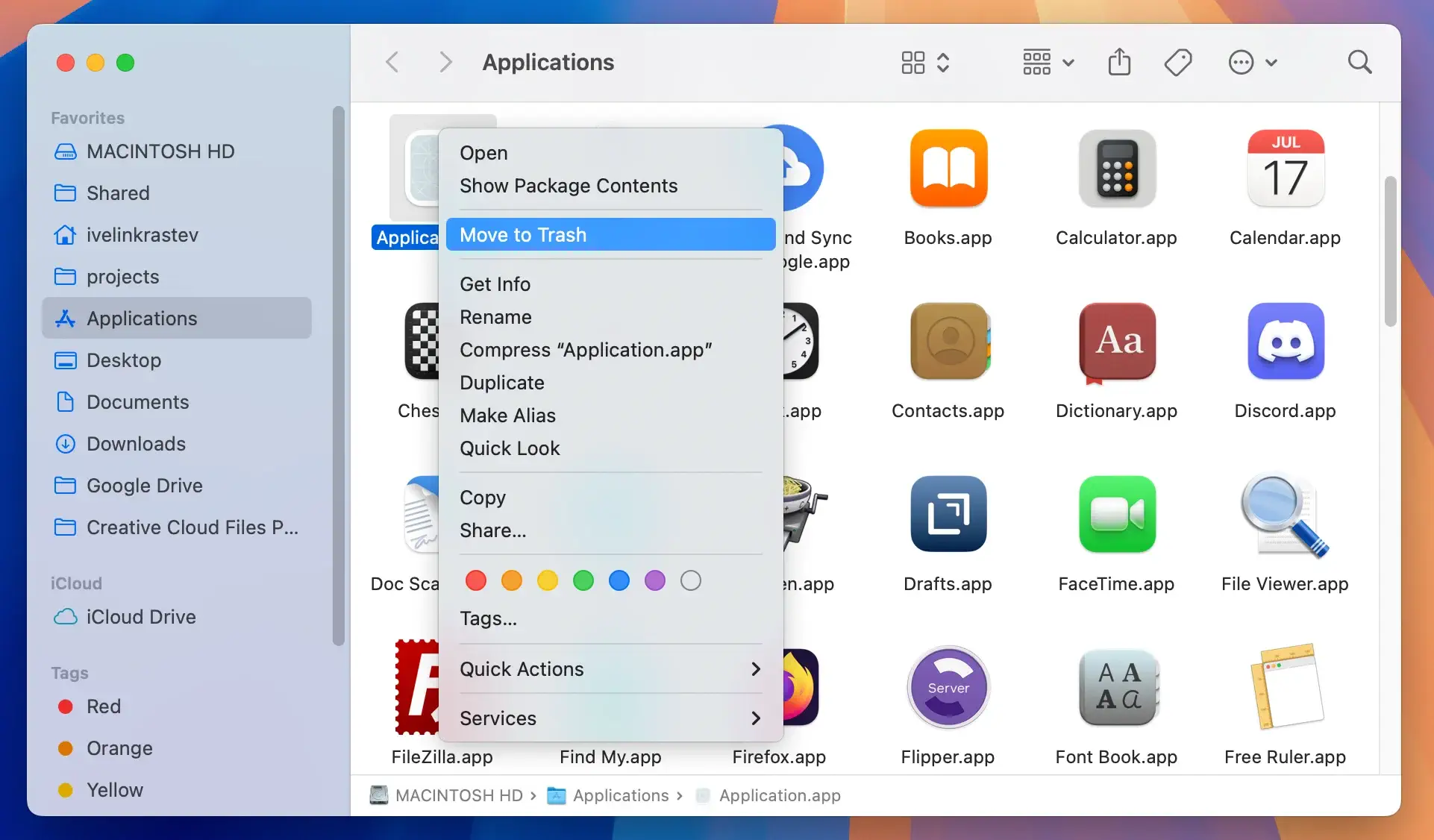
- Open your
Applicationsfolder. - Go through the list of installed apps and look for any that look out of place, have strange icons or seem suspicious. Also look out for app names that you don’t remember ever installing or using.
- Drag and drop suspicious apps you identify this way into the
Trash. - Empty the
Trash.
3. Delete any residual files linked to Cthulhu Stealer
- Open Finder and click Go > Go to Folder in the menu.
- In the dialog window that comes up, paste the following locations one after the other and hit Return after each:
/Library/LaunchAgents//Library/LaunchDaemons//Library/Application Support/~/Library/LaunchAgents/~/Library/Application Support/
- Look into each folder that opens this way and search for files or subfolders that are linked to Cthulhu Stealer and delete them manually.
- Empty the Trash to finish this step.
Responding to a Cthulhu Stealer infection
If you find yourself targeted by the Cthulhu Stealer malware on your macOS, acting quickly is crucial to protect your sensitive information.
Here are immediate steps to take and long-term strategies to minimize future risks.
- Disconnect from the Internet: Prevent the malware from sending further data by disconnecting your device from the internet.
- Scan your system: Use reputable security software to detect and remove the malware. SpyHunter for macOS is an effective choice, scanning your system for threats like Cthulhu Stealer.
- Change passwords: Immediately change passwords for sensitive accounts, especially if they were stored or possibly compromised on your device.
- Notify affected services: Contact the support teams of your financial services and online accounts to alert them of potential unauthorized access.
- Monitor for anomalies: Keep an eye on your accounts for any unusual activity that may indicate misuse of stolen data.
These steps should help mitigate the immediate damage caused by the infection.