How To Remove Qual Ransomware On Mac [Recovery Tips]
Before we dive in
Before we dive in, let's make sure you stay safe online. We created SpyHunter because your security matters to us.
Protect your computer today — download SpyHunter right here! Check out our top tips below to keep your computer safe and secure.

Ever found yourself staring at a computer screen filled with encrypted files, all ending in .qual?
Imagine the panic of losing access to all your personal files, photos, documents, and videos to Qual ransomware.
This article dives into the shadows of Qual ransomware, explaining its tactics, the risks, and how it can sneak into computers disguised as legitimate software.
What is Qual ransomware, and how does it affect your computer?
Qual ransomware is a type of malware that infiltrates computer systems, encrypting files with the .qual extension, making them inaccessible without a unique decryption key.
This ransomware variant, a member of the notorious STOP/DJVU ransomware family, specifically targets personal documents, images, videos, and other critical files.

Once the files are encrypted, the ransomware places a ransom note inside a plain-text “_readme.txt” file, demanding payment in Bitcoin to release the decryption key required to unlock the affected files.
This kind of cyberattack not only jeopardizes personal data but also demands financial ransom, putting victims in a difficult position.
Understanding the encryption of Qual ransomware
Qual ransomware employs a powerful encryption algorithm that locks files so effectively that decryption, without the specific key, is virtually impossible.
Each victim’s data is encrypted with a unique key, which is then stored on a remote server controlled by cybercriminals.
This means the only ways to retrieve the encrypted files are to pay the ransom demanded or hope for a breakthrough by cybersecurity experts or law enforcement.
Unfortunately, the use of a unique encryption key for each incident makes standard decryption tools ineffective.
Why is Qual considered a dangerous type of malware?
Qual ransomware is considered extremely dangerous due to its formidable encryption and the tactics it uses to spread, such as masquerading as legitimate software downloads.
Once it infects a computer, the ransomware not only locks valuable files but also avoids detection by disabling active antivirus programs, making it harder to remove.
Without reliable backups, recovering the encrypted and locked files becomes a practically impossible affair, as paying the ransom does not always result in data recovery.
Step-by-step guide to remove Qual ransomware
The process of handling a Qual ransomware infection requires quick and decisive steps to limit damage and recover your files securely.
Identify and isolate the infected systems
First, you must identify the infected devices. This involves scanning all systems for signs of the Qual ransomware infection.
Look out for unusual file extensions or files that don’t open as they should, which are typical signs of ransomware.
Once identified, isolate the affected systems to prevent the ransomware from spreading to networked devices.
This means disconnecting them from the internet and any internal networks. Until this is complete, do not attempt to remove the malware, as it can lead to further data corruption.
Use SpyHunter to detect and remove traces of the malware
After isolating the infected device, the next step involves cleaning it with a robust anti-malware tool.
We recommend using SpyHunter to remove Qual ransomware effectively. SpyHunter is designed to detect and eliminate ransomware and other malicious files swiftly and efficiently.
Here’s how to get started with SpyHunter:
- Download the app and complete the install as shown on your screen.
- Launch the SpyHunter app from your dock and select to perform a full system scan from the main menu.
- Examine the list of detected items and select all threats discovered, including the Qual ransomware.
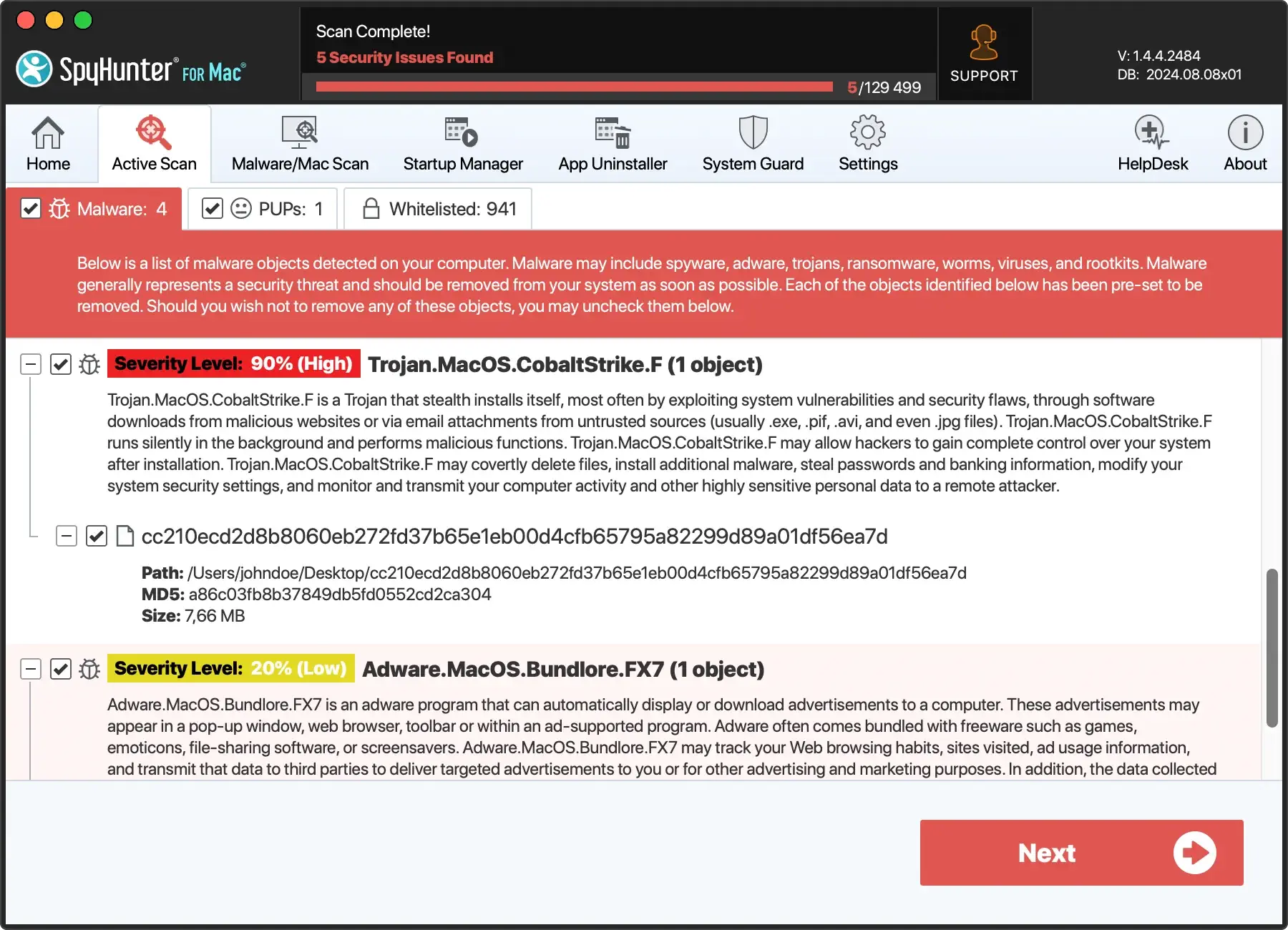
- Follow the prompts to remove the identified threats and reboot the system if prompted.
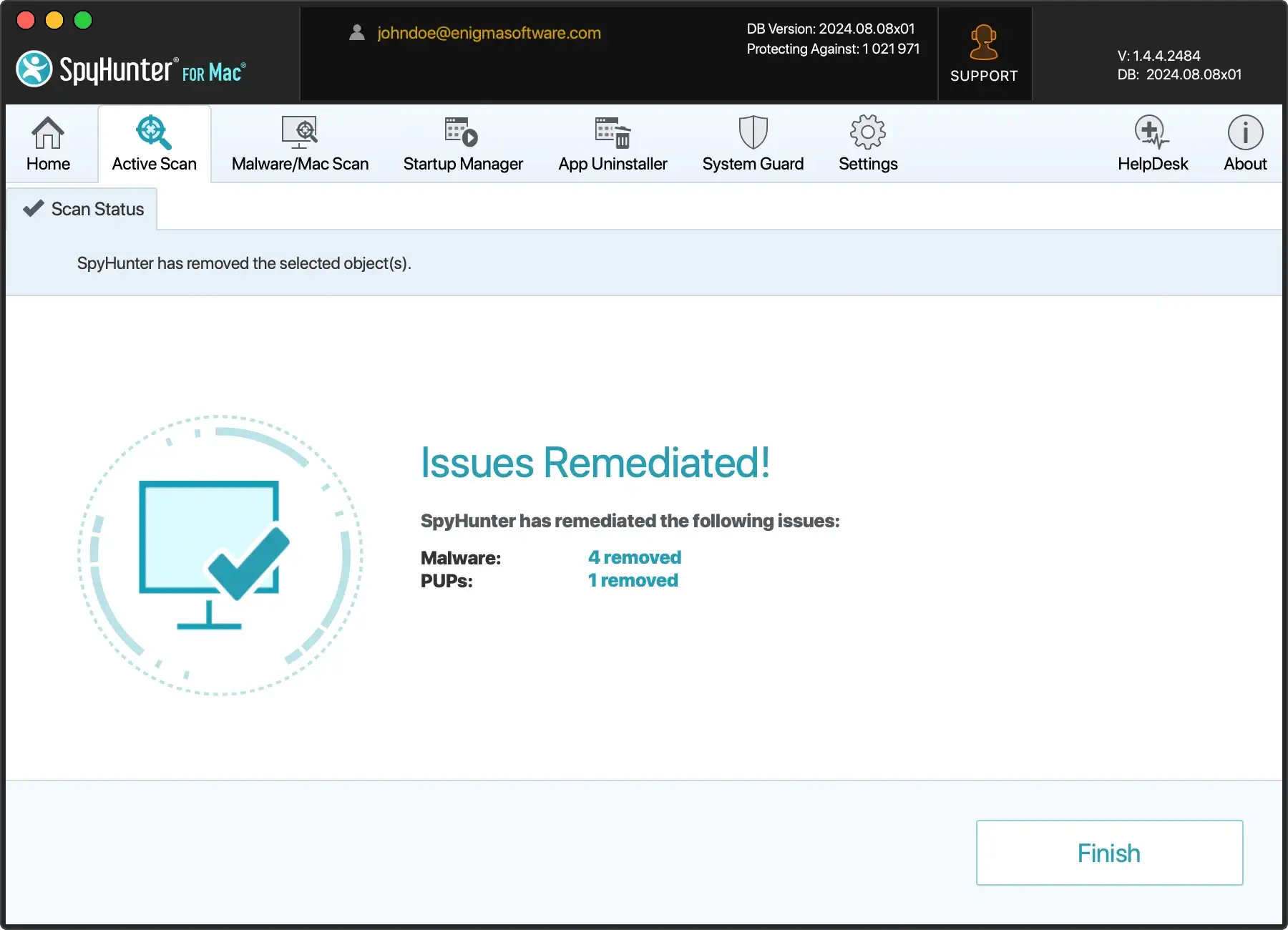
Be aware that if you use an anti-malware tool like SpyHunter after encryption has already taken place, you will not be able to recover your files.
A tool like SpyHunter can remove the ransomware from your system and protect you from future infections with its active guard, but it cannot recover files that have already been encrypted.
Recovering your files from Qual ransomware encryption
Exploring file recovery options after a Qual attack
Given the nature of most ransomware, including Qual, the only reliable solution for restoring your encrypted files remains external backups.
Most ransomware variants, especially new ones, do not have an available decryption tool available online.
Backing up your files using either external storage or the cloud is the only surefire solution to restoring all your encrypted files and encrypted data.
Is paying the ransom ever a viable option?
Paying the ransom to recover your files from Qual ransomware is generally discouraged.
Payment does not ensure that you will get your data back and further finances criminal activities. Cybersecurity experts and law enforcement alike advise against paying ransoms.
Can you prevent Qual ransomware infections?
Ransomware like Qual poses significant threats to both individual and organizational data. However, preventive steps can sharply reduce the likelihood of infection.
Keeping software up to date ensures vulnerabilities are patched, shutting down one major infection avenue exploited by attackers.
Employing robust antivirus software, such as SpyHunter, adds another layer of defense by detecting and removing malicious software before it can cause harm.
Moreover, developing a culture of caution around emails and downloads is crucial. Educating yourself and your team on recognizing suspicious links and attachments can help prevent inadvertent downloads of ransomware.
Lastly, restricting permissions on your system folders and using strong firewalls can prevent ransomware from spreading across a network if it does penetrate initial defenses.
Effective strategies to protect your data from ransomware attacks
One of the most effective strategies for protecting data is regular backup.
Backups should be performed frequently and stored offsite or on disconnected storage devices. This approach ensures that, should your data be held hostage by ransomware, you can restore it without bowing to ransom demands.
Besides backups, enabling multi-factor authentication wherever possible can greatly enhance your security posture. MFA adds an additional verification step, which makes unauthorized access to your systems and data significantly more challenging for attackers.
Top tips for enhancing your cybersecurity posture
To fortify your defenses against ransomware and other cyber threats, start by securing your network.
Refine your email security practices by learning to recognize phishing attempts, which are a common entry point for ransomware.
Regular software updates and the use of strong, unique passwords across all user accounts are equally important.
FAQs about dealing with Qual ransomware
How can I identify a Qual ransomware infection?
Ransomware like Qual typically announces its presence through a ransom note and by changing the extensions of encrypted files.
For instance, if you discover files assuming a new extension, such as .qual, it’s a significant indicator of a Qual ransomware infection.
Additionally, ransom notes named _readme.txt, containing ransom payment instructions, often appear in every folder containing encrypted files.
What should I do immediately after detecting Qual ransomware?
Once you detect the presence of Qual ransomware on your computer, your immediate step should be to isolate the infection to prevent further damage.
Disconnect your device from the internet and external storage devices to stop the ransomware from spreading.
Next, run a full system scan using a robust cybersecurity software to identify and remove the ransomware components.
It’s crucial to eliminate the ransomware before attempting any file recovery processes to ensure that the malware does not re-encrypt recovered files or spread further.
How does SpyHunter help in recovering from Qual ransomware?
SpyHunter can effectively assist in the removal of Qual ransomware from your computer. Here’s how SpyHunter supports the recovery process:
- Detection and removal: SpyHunter scans your system to detect and isolate components of the Qual ransomware. By thoroughly removing ransomware traces, it prevents further encryption of your files and additional harm to your system.
- Safety from reinfection: Post-cleanup, SpyHunter can safeguard your system from future attacks by providing real-time protection against threats, reducing the risk of another ransomware infection.
Note that while SpyHunter excels in malware removal and infection prevention, it does not decrypt files that have already been affected by encryption.
Protecting against future threats
Essential tools and practices to safeguard your systems
Securing information systems begins with the adoption of essential tools and practices designed to protect against cyber threats.
Fundamental measures include the installation of comprehensive cybersecurity software like SpyHunter, which provides real-time protection against malware, spyware, and potentially unwanted programs.
It’s also vital to keep all software up-to-date. Regular updates help patch security vulnerabilities that could be exploited by attackers. Additionally, organizations should conduct frequent training sessions to educate their employees about cybersecurity best practices and the importance of strong, unique passwords.
Regular backups: Your safety net against ransomware attacks
Regular data backups are indispensable in protecting against ransomware attacks and recovering files.
By maintaining up-to-date copies of important information, organizations can restore their systems without succumbing to the demands of ransomware attackers.
To be effective, backups should be performed daily and stored in multiple locations, including external drives and the cloud.
This strategy not only safeguards data but also ensures that it can be recovered quickly and efficiently after an attack, thereby minimizing downtime and operational losses.